skynethosting
Active Member
Since December 2023, multiple actors have initiated operations using the CLINKSINK drainer to illicitly acquire funds and tokens from Solana (SOL) cryptocurrency users. Drainers are harmful scripts and smart contracts that enable the drainage of funds or digital assets like non-fungible tokens from victims' wallets through deceitful transactions.
These campaigns involved at least 35 affiliate IDs linked to a drainer-as-a-service (DaaS) system utilizing CLINKSINK. The DaaS's operator(s) supply these drainer scripts to their affiliates, receiving about 20% of the ill-gotten gains in return. The total estimated value of assets stolen in these recent operations is over $900,000 USD.
Details of the CLINKSINK Drainer Operations:Recent activities saw threat actors leveraging social media and messaging platforms, such as X and Discord, to spread phishing pages with cryptocurrency themes to engage victims with the CLINKSINK drainer. These phishing sites, posing as legitimate crypto resources like Phantom, DappRadar, and BONK, used various fake token airdrop lures to load malicious CLINKSINK JavaScript code, thereby enabling wallet connections and fund theft.
Victims visiting these phishing sites are tricked into linking their wallets to claim a supposed token airdrop. Upon wallet connection, they are prompted to authorize a transaction, unknowingly granting the drainer service access to siphon their funds.
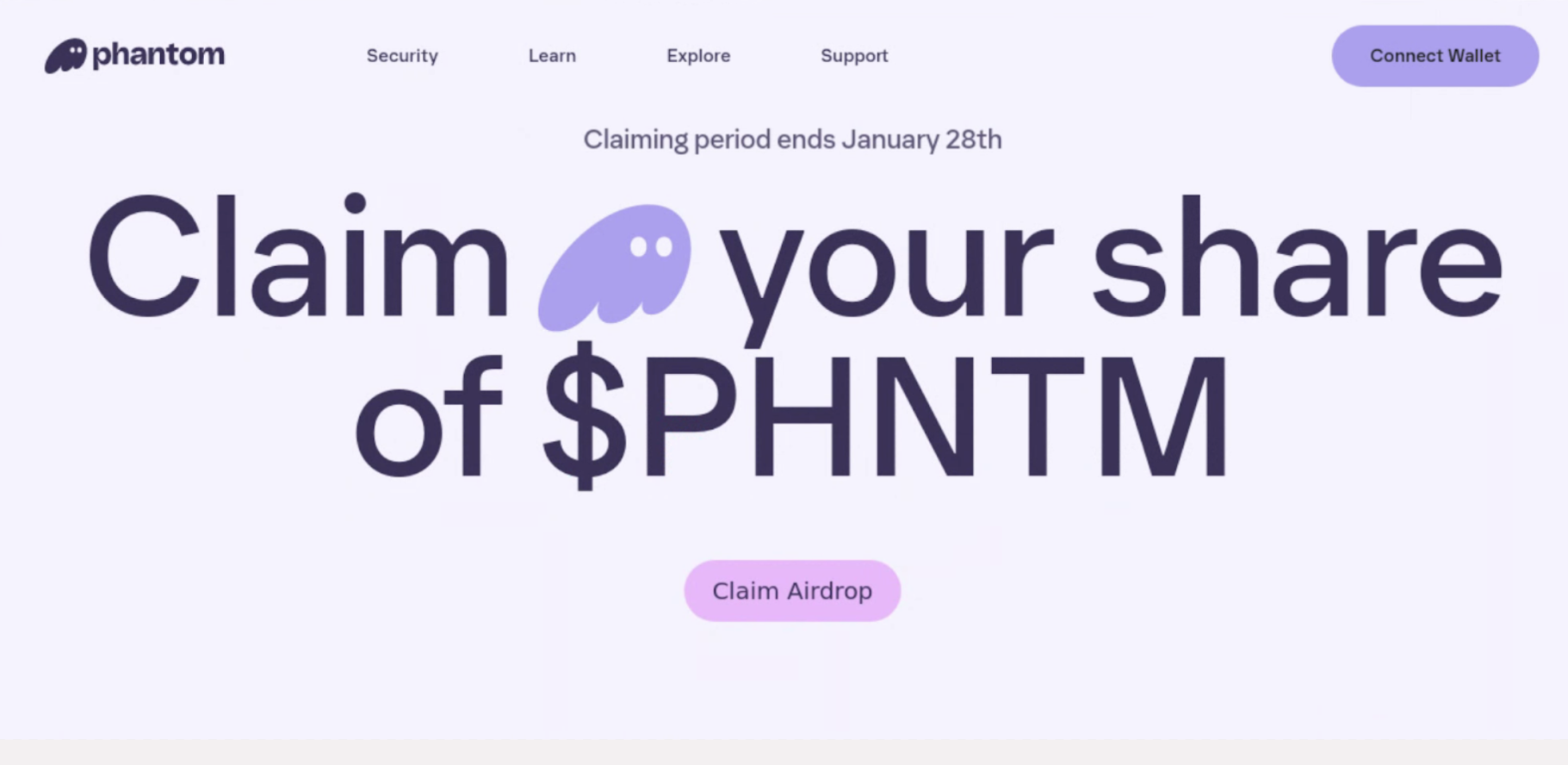
Screenshot of $PHNTM airdrop-themed phishing page
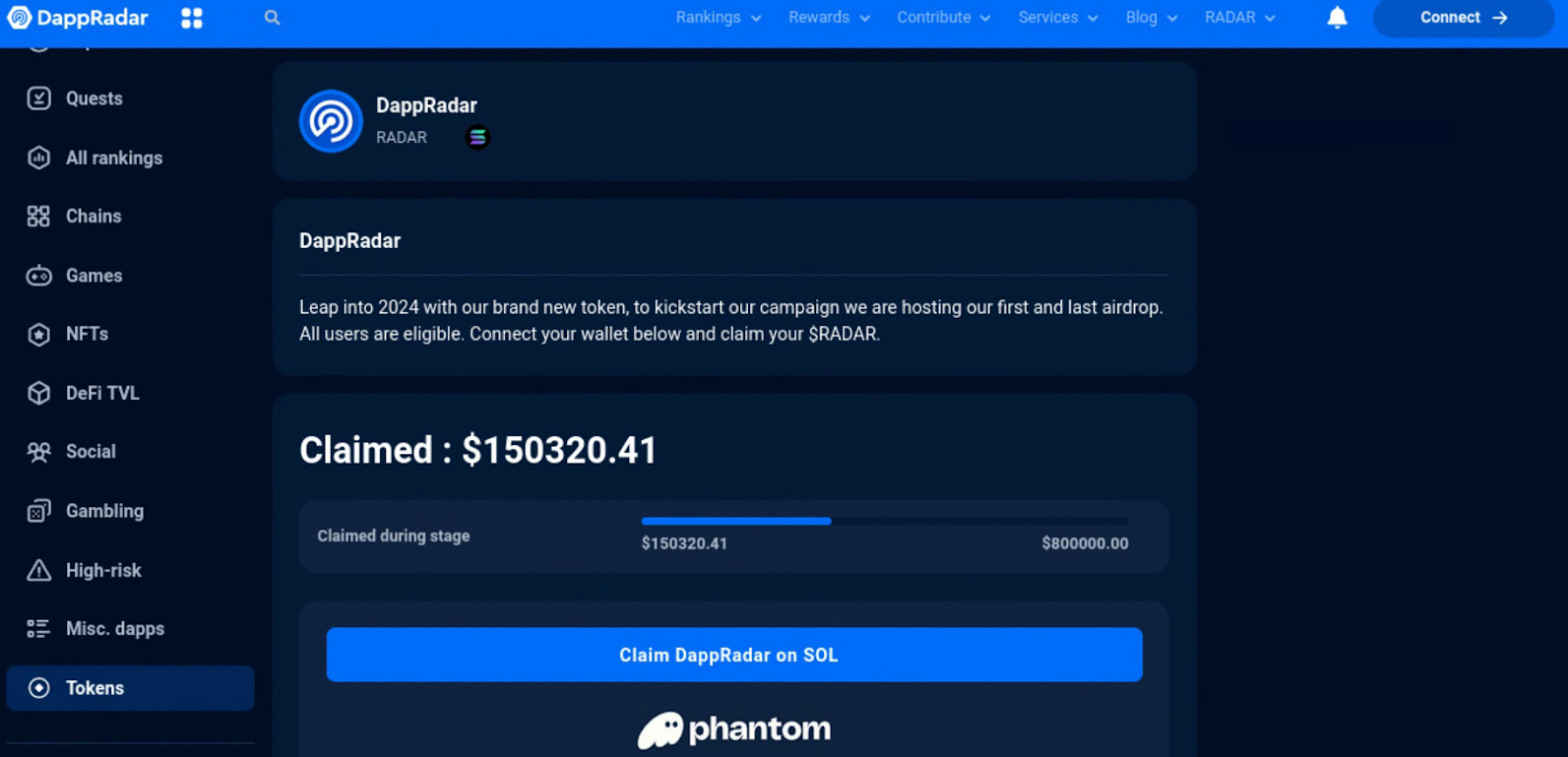
Screenshot of DappRadar-themed phishing page
Screenshot of BONK-themed phishing page

These campaigns involved at least 35 affiliate IDs linked to a drainer-as-a-service (DaaS) system utilizing CLINKSINK. The DaaS's operator(s) supply these drainer scripts to their affiliates, receiving about 20% of the ill-gotten gains in return. The total estimated value of assets stolen in these recent operations is over $900,000 USD.
Details of the CLINKSINK Drainer Operations:Recent activities saw threat actors leveraging social media and messaging platforms, such as X and Discord, to spread phishing pages with cryptocurrency themes to engage victims with the CLINKSINK drainer. These phishing sites, posing as legitimate crypto resources like Phantom, DappRadar, and BONK, used various fake token airdrop lures to load malicious CLINKSINK JavaScript code, thereby enabling wallet connections and fund theft.
Victims visiting these phishing sites are tricked into linking their wallets to claim a supposed token airdrop. Upon wallet connection, they are prompted to authorize a transaction, unknowingly granting the drainer service access to siphon their funds.
Screenshot of $PHNTM airdrop-themed phishing page

Screenshot of DappRadar-themed phishing page

Screenshot of BONK-themed phishing page



