Proof of moreleech/leafleech hacking clients - What happened?
What you are going to read in this post, usually doesn't happen, because we don't disclose evidence to users, but since we care, we feel it's necessary to protect our users, by making this warning post.
STAFF INVESTIGATION
If you are not ready to read huge ass post, don't bother, missing one part will make your image about this case distorted. We invested our free time to go through 40 days of investigation, and one whole day combining all evidence into one meaningful post.
This is a letter, which is targetting scamming group, coming from Bangladesh, under several names, previously advertising on WJunction. They are/were known as leafleech/moreleech/sparklinghost/newrapidleech and probably more they got up and shut down.
So, once we banned them for hacking into users account, they started trashing us.
It is time for the truth.
THE TRUTH
All started with leafleech and heart_tracker. heart_tracker complained about 40 days ago, that leafleech banned him and didn't want to refund them. So, I took the case.
We got several reports from bistarito@musafirboy, regarding trashing his thread with false comments, which were deleted. We deleted them. And then, we get report that heart_tracker was sending some random insulting messages to respected members and even administration. Of course, no one in his common sense does that, since that means instant ban. So I was reserved about whether he did it or not.
After all, he was using totally unsecured service, that never heard of password encryption, which is the main flaw in any Rapidleech. I was convinced it has to do something with revenge, we all know what kind of people is hanging there, and that competition will do anything, from DDOS, to hacking, just to put others down. On the other hand, WJunction staff has no benefit in doing so.
Now, for the record:
heart_tracker is pakistani
bistarito@musafirboy
x7x aka BT7
BiGG_BoSS
SparklingHost
Are nicknames are logging from Bangladesh, have criss-crossed matching IPs.
Main guy in all this is BiGG_BoSS character, and his email latestdownload7@gmail.com which he used to register on WJunction.
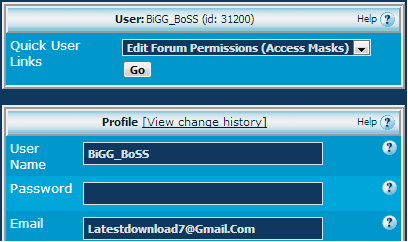
Moreleech WHMCS license is registered with same email Latestdownload7@gmail.com <--this is how we know x7x is BiGG_BoSS
It is undeniable proof of connection.
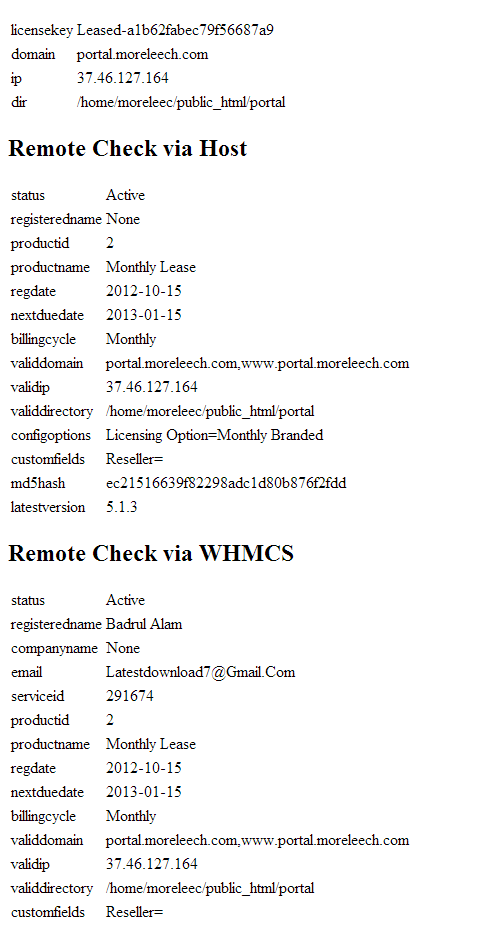
Bigg_Boss have site named warez-lab.com, that he used to send hacking messages to heart_tracker, proof can be found here:
Yahoo message header:
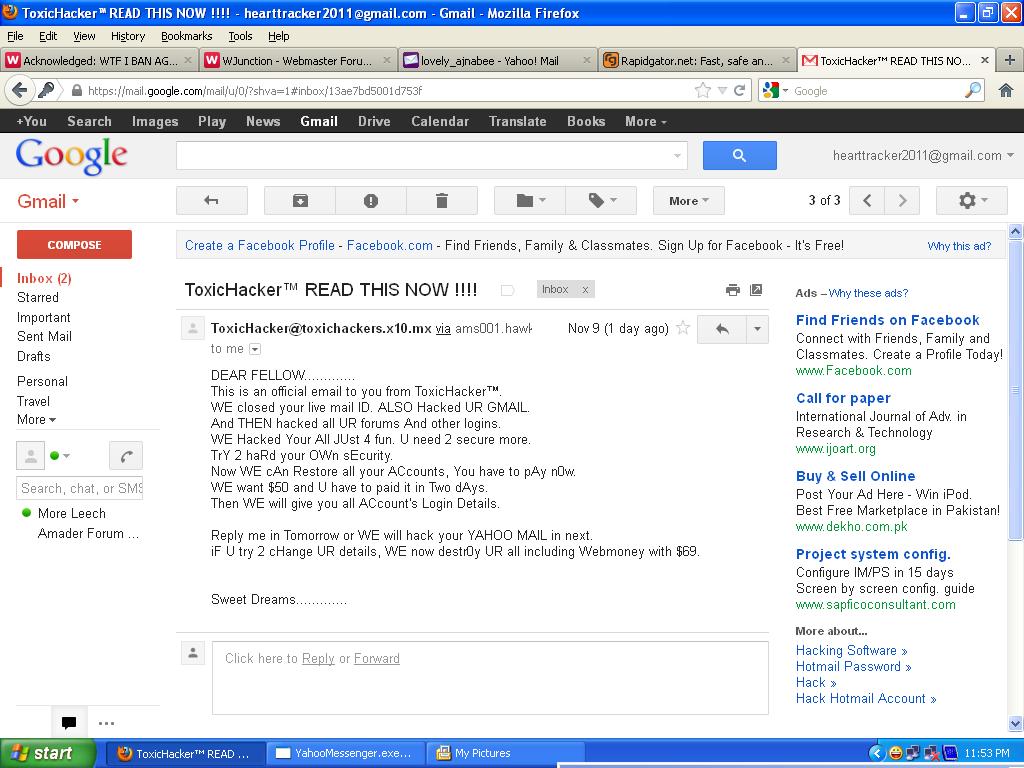
Gmail message header:
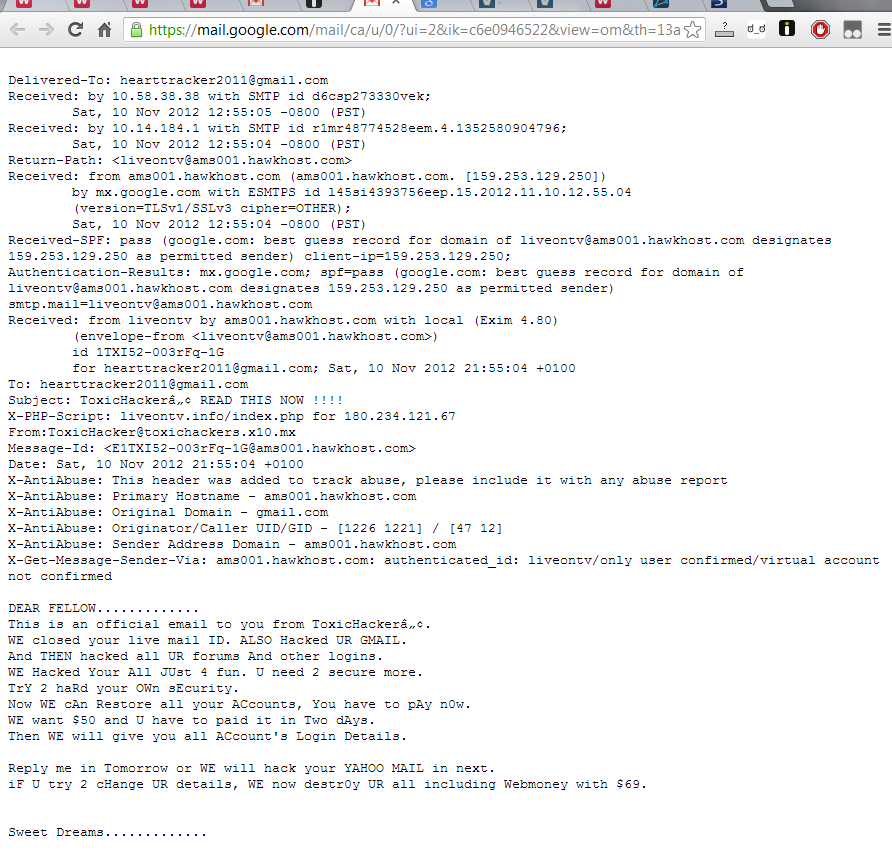
Proof that it's BiGG_BoSS domain is here <-this is how we know bistarito@musafirboy is BiGG_BoSS
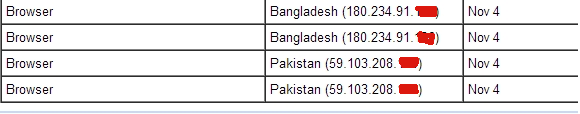
Also IP logins from heart_trackers gmail account, show that Bangladeshi was accessing his gmail account:
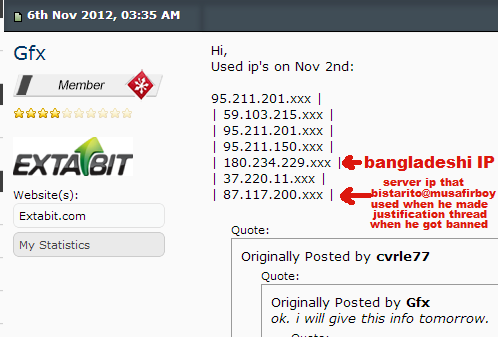
We also got confirmation from Extabit (Thanks to Gfx), that this is the IP that got accessed to heart_trackers extabit account
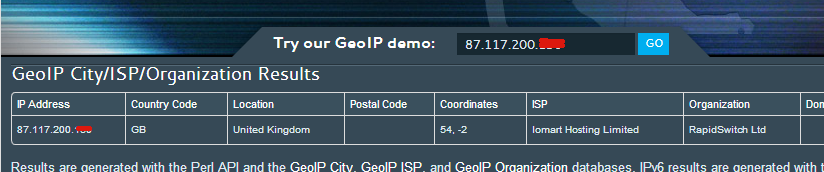
Same IP that shows in heart_trackers posts with abusive messages, shows as IP in bistaritos justification thread:
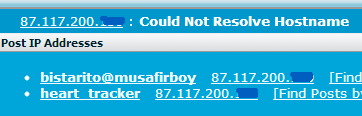
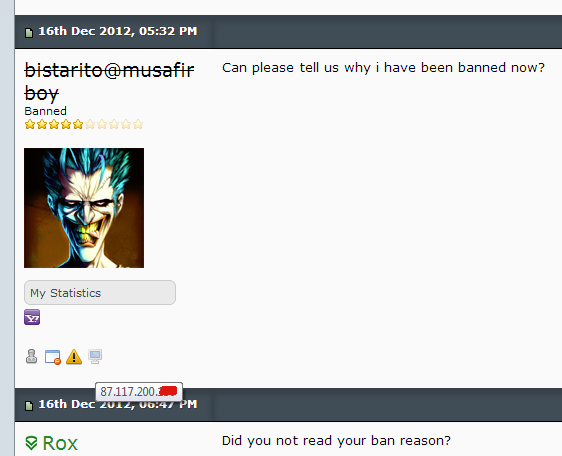
From this, we know that bistarito used server to access WJ, and post abusive messages using heart_trackers account. Since IP is static, and belongs to RapidSwitch, we know it's not a coincidence.
Also, they (moreleech) are showing up on WJ at the same date when bistarito got unbanned, on 12th November, which is actually a new service from same 'kitchen' that was a backup plan, in case bistarito doesn't get unbanned.
MOTIVES
Motives are also required for someone to do this, and motives are obvious. heart_tracker ruined their thread with negative replies, and as revenge, they picked up all his data he entered in rapidleech, accessed all his accounts, changed his passwords and emails. This can also be confirmed by Rapidgator, Extabit, and all other services heart tracker was using through moreleech/leafleech rapidleech, where he was needded to enter own details in unencrypted system, where staff had access to his accounts at any given time. They did this after bistaritos case, 40 days ago, and another time, just a few days ago.
DECISION TIME
So, anyone who thinks we made our decision, just to put them with no reason out of business, think again. Do you really want to use a service that has access to all your file host details all the time, where it was proven, that they are taking customers details and play with them?
What you are going to read in this post, usually doesn't happen, because we don't disclose evidence to users, but since we care, we feel it's necessary to protect our users, by making this warning post.
STAFF INVESTIGATION
If you are not ready to read huge ass post, don't bother, missing one part will make your image about this case distorted. We invested our free time to go through 40 days of investigation, and one whole day combining all evidence into one meaningful post.
This is a letter, which is targetting scamming group, coming from Bangladesh, under several names, previously advertising on WJunction. They are/were known as leafleech/moreleech/sparklinghost/newrapidleech and probably more they got up and shut down.
So, once we banned them for hacking into users account, they started trashing us.
It is time for the truth.
THE TRUTH
All started with leafleech and heart_tracker. heart_tracker complained about 40 days ago, that leafleech banned him and didn't want to refund them. So, I took the case.
We got several reports from bistarito@musafirboy, regarding trashing his thread with false comments, which were deleted. We deleted them. And then, we get report that heart_tracker was sending some random insulting messages to respected members and even administration. Of course, no one in his common sense does that, since that means instant ban. So I was reserved about whether he did it or not.
After all, he was using totally unsecured service, that never heard of password encryption, which is the main flaw in any Rapidleech. I was convinced it has to do something with revenge, we all know what kind of people is hanging there, and that competition will do anything, from DDOS, to hacking, just to put others down. On the other hand, WJunction staff has no benefit in doing so.
Now, for the record:
heart_tracker is pakistani
bistarito@musafirboy
x7x aka BT7
BiGG_BoSS
SparklingHost
Are nicknames are logging from Bangladesh, have criss-crossed matching IPs.
Main guy in all this is BiGG_BoSS character, and his email latestdownload7@gmail.com which he used to register on WJunction.

Moreleech WHMCS license is registered with same email Latestdownload7@gmail.com <--this is how we know x7x is BiGG_BoSS
It is undeniable proof of connection.

Bigg_Boss have site named warez-lab.com, that he used to send hacking messages to heart_tracker, proof can be found here:
Yahoo message header:
From ToxicHacker@toxichackers.x10.mx Fri Nov 9 15:20:28 2012
X-Apparently-To: lovely_ajnabee@yahoo.com via 67.195.13.216; Fri, 09 Nov 2012 15:20:29 -0800
Return-Path: <liveontv@ams001.hawkhost.com>
Received-SPF: none (domain of ams001.hawkhost.com does not designate permitted sender hosts)
aWNpYWwgZW1haWwgdG8geW91IGZyb20gVG94aWNIYWNrZXLihKIuIFdFIGNs
b3NlZCB5b3VyIGxpdmUgbWFpbCBJRC4gQUxTTyBIYWNrZWQgVVIgR01BSUwu
IEFuZCBUSEVOIGhhY2tlZCBhbGwgVVIgZm9ydW1zIEFuZCBvdGhlciBsb2dp
bnMuIFdFIEhhY2tlZCBZb3VyIEFsbCBKVXN0IDQgZnVuLiBVIG5lZWQgMiBz
ZWN1cmUgbW9yZS4gVHJZIDIgaGFSZCB5b3VyIE9XbiBzRWN1cgEwAQEBAQ--
X-YMailISG: Sh9rz5wWLDvlVDaPOmYXHDTFv6yDiSPlx4V94pGddO1_20Ld
0OQKE8vgd1YK144fQnPwYJOL_7YX1ndDBuVJ9t7l1kbYhfYOaB2uZ.bCMD6B
FCgvt2349y9Fe9QtlcGaA7smKx0e8WkQBUwy8XyfoOKo3CQXPTaiGv.dI_Ou
N8gpBGWxK2I1_PL_Oduq4tBD60gDtVFQ1i7kwNfGDcvzkHK2usaRE3kxaeJ7
e2Qj0O9Z__TOxD8fiprQgy7MvetlIqSdlXvg8bISpp6MoQBY.mWCgYviLeZ4
uEL6T_gzRPZzhdDNXDsmALsWKBZ82VjvN0r1feVVXvNxpuzTM3sEdQDLpOh2
npxBrpzeMABGMyoasVZYCtfmKKeWlwKnLtUqivOHqcBIo.D_bZY0pbKcBDls
ZiqKdXMVkJ1fReA1TMssD6.2s5IOighh2iaW2Ug2mtMsg3rhvmKi82sB5pfy
jU3ipoOCZ1lweYgbBm6qAORW0HSxSyrJVRHy5mCzUTOY1zKSV8AyOe3ISFgx
9t1yJ.hLaFwDjWKBoACFDOWEXXEWT.CHf6Tbw.fb8aDlx0o0VT8D8AsYYBqj
aZwWjTGp1yweYBKy4N2yCbvMMpmRFKhkzV4JcBOD3t94fQtqAT.JHH5wJoeu
zxFalpTYy91ZmKQpxz.3_i1s_F_Q.XB53IE0.xYduAZCodzQ4IhK4K8eCzvo
wtAf2ZYm195z9ut1IThI25n44JqeYCyp0_CpBLyfgp9nIK9DPFCpFSMdiWWx
Cf1opjVGeufJcmfH6E.wcKqGQYNULOELovWJFgy7d3uULC2BjEnBW6ymnvGS
QChophGI9lU0Ii_Eqljc5JDZXtt94kXIpX6WC8ZRgrmZn.FqO1mJf7bicj4s
rIMzSlzhZu6OXB6euQzWBgbFf_scSx6Lb0V.bGFeE5E1qw32Se3VEaCFRocu
EMQIwtxbLx9tSk1SbPy4q0lJMsofjRgg.J2dFHBWbfGvNULYQVWT7K47o1m5
8mqKpl5TFzM9InFx6FB8T3zonNBYFVG1BfuxKJY18ST0HtkJwWkT334z9.He
o06NG69o74SnFJngXE2q91DWzqyUeuJOrF1I72Zmc6L8Mdgy2uzT4zQtqlXn
f6SsUM.tGzEv5vDvtc.f6bb1fGUpGv3r53DDwFRxwMqhusw.cITgJV1i7pGn
r5_woYiemrvbu4qFPHmxCG.hx68fbaHZJD8-
X-Originating-IP: [159.253.129.250]
Authentication-Results: mta1306.mail.bf1.yahoo.com from=; domainkeys=neutral (no sig); from=toxichackers.x10.mx; dkim=neutral (no sig)
Received: from 127.0.0.1 (EHLO ams001.hawkhost.com) (159.253.129.250)
by mta1306.mail.bf1.yahoo.com with SMTP; Fri, 09 Nov 2012 15:20:29 -0800
Received: from liveontv by ams001.hawkhost.com with local (Exim 4.80)
(envelope-from <liveontv@ams001.hawkhost.com>)
id 1TWxsC-0034r1-ER
for lovely_ajnabee@yahoo.com; Sat, 10 Nov 2012 00:20:28 +0100
To: lovely_ajnabee@yahoo.com
Subject: ToxicHacker<E2><84><A2> READ THIS NOW !!!!
X-PHP-Script: warez-lab.com/index.php for 5.9.57.56
From:ToxicHacker@toxichackers.x10.mx
Message-Id: <E1TWxsC-0034r1-ER@ams001.hawkhost.com>
Date: Sat, 10 Nov 2012 00:20:28 +0100
X-AntiAbuse: This header was added to track abuse, please include it with any abuse report
X-AntiAbuse: Primary Hostname - ams001.hawkhost.com
X-AntiAbuse: Original Domain - yahoo.com
X-AntiAbuse: Originator/Caller UID/GID - [1226 1221] / [47 12]
X-AntiAbuse: Sender Address Domain - ams001.hawkhost.com
X-Get-Message-Sender-Via: ams001.hawkhost.com: authenticated_id: liveontv/only user confirmed/virtual account not confirmed
Content-Length: 590


Gmail message header:

Proof that it's BiGG_BoSS domain is here <-this is how we know bistarito@musafirboy is BiGG_BoSS
Also IP logins from heart_trackers gmail account, show that Bangladeshi was accessing his gmail account:

We also got confirmation from Extabit (Thanks to Gfx), that this is the IP that got accessed to heart_trackers extabit account

Same IP that shows in heart_trackers posts with abusive messages, shows as IP in bistaritos justification thread:


From this, we know that bistarito used server to access WJ, and post abusive messages using heart_trackers account. Since IP is static, and belongs to RapidSwitch, we know it's not a coincidence.

Also, they (moreleech) are showing up on WJ at the same date when bistarito got unbanned, on 12th November, which is actually a new service from same 'kitchen' that was a backup plan, in case bistarito doesn't get unbanned.
MOTIVES
Motives are also required for someone to do this, and motives are obvious. heart_tracker ruined their thread with negative replies, and as revenge, they picked up all his data he entered in rapidleech, accessed all his accounts, changed his passwords and emails. This can also be confirmed by Rapidgator, Extabit, and all other services heart tracker was using through moreleech/leafleech rapidleech, where he was needded to enter own details in unencrypted system, where staff had access to his accounts at any given time. They did this after bistaritos case, 40 days ago, and another time, just a few days ago.
DECISION TIME
So, anyone who thinks we made our decision, just to put them with no reason out of business, think again. Do you really want to use a service that has access to all your file host details all the time, where it was proven, that they are taking customers details and play with them?



